What is Cisco ISE?
Cisco Identity Services Engine
(ISE) is a server-based product, either a Cisco ISE appliance or Virtual
Machine that enables the creation and enforcement of access polices for
endpoint devices connected to a company’s network.
ISE is a network access/admission control
solution. It enables a dynamic and automated approach to policy enforcement
that simplifies the delivery of highly secure network access control.
- The profiling feature of ISE provides dynamic detection and classification of endpoints connected to the network.
- ISE is capable of giving the information of the type of medium through which endpoints get connected to the network i.e., Wired (802.1x or MAB), Wireless (802.1x or MAB), or Remote Access (VPN).
- It is also possible to know where the user/endpoint is connecting from i.e., Head Office, branch office, regional office, remote, first floor of head office, etc.
- ISE uses posture to check the state of endpoints that are connecting to a network for compliance with corporate security policies.
What can you do with Cisco
ISE?
In simple terms you can control
who can access your network and when they do what they can get access to. It
can authenticate wired, wireless and vpn users and can scale to millions of
endpoints. Based on many factors including the validity of a certificate, mac
address or device profiling you can identify a machine and determine which vlan
that machine is placed into. Any devices that do not pass authorization will be
placed into a guest vlan or denied access to the network.
All this information is logged and
you can instantly get a view of what is connected to your network at any time.
Features
- Secure Wired Access
- Secure Wireless Access
- Secure Remote Access VPN
- Guest Access Management
- Asset Visibility (Profiling)
- Posture Compliance
- Bring Your Own Device (BYOD)
- Threat Containment
- Segmentation
- Security Ecosystem Integrations
- Device Administration (TACACS)
Node: A node is an individual instance that runs the
Cisco ISE software. Cisco ISE is available as an appliance (hardware) and as a
virtual appliance. Any device or virtual machine that runs Cisco ISE software
is an ISE node
Persona: The persona of a node determines the services
provided by the node. A Cisco ISE node can assume any of the following personas:
Administration, Policy Service, Monitoring, and pxGrid.
Service: A service is a specific feature that a persona
provides.
Role: Determines if a node is standalone, primary, or
secondary node. This applies only to Administration and Monitoring nodes.
A Cisco ISE node can provide various services based on the persona that
it assumes. Each node in a deployment can assume the Administration, Policy
Service, pxGrid, and Monitoring personas. In a distributed deployment, you can
have the following combination of nodes on your network:
- Primary and secondary Administration nodes for high availability
- A pair of Monitoring nodes for automatic failover
- One or more Policy Service nodes for session failover
- One or more pxGrid nodes for pxGrid services
- A Monitoring and Troubleshooting Node (MnT) provides monitoring and troubleshooting services.
- This node is having a Monitoring persona. A Cisco ISE node with the Monitoring persona functions as the log collector and stores log messages from all the Administration and Policy Service nodes in a network.
- This persona provides advanced monitoring and troubleshooting tools that you can use to effectively manage a network and resources.
- Cisco ISE allows you to have a maximum of two nodes with this persona, and they can take on primary or secondary roles for high availability. Both the primary and secondary Monitoring nodes collect log messages. In case the primary Monitoring node goes down, the secondary Monitoring node automatically becomes the primary Monitoring node.
- At least one node in your distributed setup should assume the Monitoring persona. We recommend that you do not have the Monitoring and Policy Service personas enabled on the same Cisco ISE node.
Administration Node:
- An Administration node provides administrative services i.e., handling of policies and system-related configurations etc. Such node is said to have the Administration persona.
- A Cisco ISE node with the Administration persona allows you to perform all administrative operations on Cisco ISE.
- It handles all system-related configurations that are related to functionality such as authentication, authorization, and accounting.
- In a distributed deployment, you can have a maximum of two nodes running the Administration persona.
- The Administration persona can take on the standalone, primary, or secondary role.
Policy Service Node:
- A Cisco ISE node with the Policy Service persona provides network access, posture, guest access, client provisioning, and profiling services.
- This persona evaluates the policies and makes all the decisions.
- You can have more than one node assume this persona. Typically, there would be more than one Policy Service node in a distributed deployment.
- All Policy Service nodes that reside in the same high-speed Local Area Network (LAN) or behind a load balancer can be grouped together to form a node group. If one of the nodes in a node group fails, the other nodes detect the failure and reset any URL-redirected sessions.
- At least one node in your distributed setup should assume the Policy Service persona.
- You can use Cisco pxGrid to share the context-sensitive information from Cisco ISE session directory with other network systems such as ISE Eco system partner systems and other Cisco platforms.
- The pxGrid framework can also be used to exchange policy and configuration data between nodes like sharing tags and policy objects between Cisco ISE and third party vendors, and for other information exchanges.
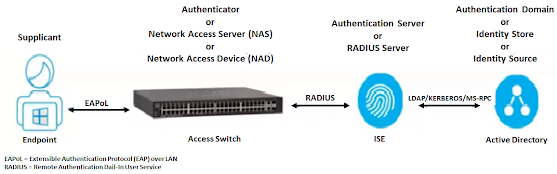
RADIUS Terminologies
Supplicant is a client device (i.e., laptop) that requests network
access. It’s sometimes also referred to as the software running on the client
device that provides credentials to the authenticator.
Authenticator is a network access device that provides network services and to which the supplicant port is connected. An authenticator can be an Access Switch, a Wireless LAN Controller (WLC), or a VPN Concentrator (i.e., Remote Access VPN Firewall)
Authentication Server is a RADIUS/AAA server that performs the actual authentication of the client.
Authentication Domain is an identity store or an identity management database (i.e., Active Directory) that a RADIUS Server can use for verifying client credentials.
Deployment Types
Standalone Deployment: Any ISE deployment with a single ISE node is a standalone deployment. The single node in this case will be running all the personas i.e., Administration, Monitoring, and Policy Service.
Distributed Deployment: Further classified as:
Small Network Deployment:
- The smallest Cisco ISE distributed is the small network deployment. It consists of two ISE nodes with each node running all the personas.
- One node will function as the primary node, while other will function as the secondary node.
- It’s just like having two standalone nodes but in this case the administration and monitoring personas will have designated role i.e., primary, and secondary.
- All the policy service personas present in an ISE deployment will always be active.
|
|
ISE Node 1 |
ISE Node 2 |
|
Deployment Style
1 |
Primary Admin Primary
Monitoring Policy Service |
Secondary Admin Secondary
Monitoring Policy Service |
|
Deployment Style 2 |
Primary Admin Secondary
Monitoring Policy Service |
Secondary Admin Primary
Monitoring Policy Service |
Medium-Sized Network Deployment:
- In a medium-sized deployment, the Administration and Monitoring personas will co-exist on the same node while the Policy Service personas will run on dedicated nodes.
- Two nodes will be dedicated to run both Administration and Monitoring personas, and the role of primary and secondary will be distributed among the two nodes.
- At least, one node must be dedicated to running Policy Service, but this deployment type can accommodate up to 5 Policy Service Nodes (PSN).
|
|
|
|
Mandatory |
Optional |
|||
|
ISE Node |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
|
Deployment Style
1 |
Pri Admin Pri MnT |
Sec Admin Sec MnT |
PSN |
PSN |
PSN |
PSN |
PSN |
|
Deployment Style 2 |
Pri Admin Sec MnT |
Sec Admin Pri MnT |
PSN |
PSN |
PSN |
PSN |
PSN |
Large Network Deployment:
- In a large network deployment, the Administration, Monitoring and Policy Service personas will all run on a dedicated node.
- This type of deployment can accommodate from 1 to 50 PSNs.
- If you have multiple PSNs in the same location, you may want to consider placing them behind a load balancer.
Operation Overview of 802.1x Authentication
Using ISE as Radius Server
- When an endpoint (Supplicant) first connects to the LAN, it will send EAPoL-Start message to a multicast group to identify the Authenticator (access switch).
- The authenticator will send back EAP-Request Identity message which is used to request identity from the Supplicant (endpoint). Note that EAP transaction can be initiated by the supplicant(endpoint) or the authenticator (switch).
- The switch sends out EAP-Request Identity periodically, even before receiving an EAPoL-Start message.
- The supplicant then provides its identity i.e., username in an EAP-Response to the switch (authenticator).
- The authenticator (switch) forwards the information received from the supplicant (endpoint) to the Authentication Server (Radius Server, in this case ISE PSN).
- The authenticator (switch) will create a Radius Access-Request message and forward the message to the Authentication Server (ISE PSN), the authentication server (PSN) will send back a RADIUS Access-Challenge message to the switch (Authenticator).
- The Authenticator (switch) receives the Access-Challenge message from the Authenticator Server (PSN) and use it to prepare a EAP-Request message (EAP-Request Auth) and forward that message to the Supplicant (endpoint).
- The purpose of the EAP-Request message is to verify that the supplicant can support the EAP method suggested by the Authentication Server (PSN). If the EAP authentication method is supported by the Supplicant, it sends an EAP-Response (user credentials) back to the Authenticator.
- The Authenticator/Switch then use it to prepare a response to the RADIUS Access-Challenge and forward it back to the Authentication Server (PSN).
- If the Authentication Server (PSN) successfully verifies the user credentials. The Authentication Server will send a RADIUS Access-Accept message to the Authenticator (Switch).
- If the credentials are wrong, the Authentication Server will send a RADIUS Access-Reject message to the Authenticator.
- Once the Authenticator receive RADIUS Access-Accept from the Authentication Server, the Authenticator will send back a EAP Success message to the supplicant.
- The Authenticator will then set the switch port to authorized i.e., open the switch port.
- The type or level of authorization given to the specific endpoint on the switch port will depend on the Change of Authorization (CoA) received by the Authenticator.
- Depending on the authorization profile configured on the PAN, the switch may be requested to download ISE preconfigured ACL (DACL) and apply it to the specific endpoint on the specific port, ISE may request the switch to apply a Filter-ID which have been pre-configured on the Switch (ISE will only send the name of the ACL to the switch), ISE may also instruct the switch to dynamically change the VLAN of the switch port.
- In a wireless scenario, ISE can instruct the WLC to apply a preconfigured Airespace ACL (ISE will only send the ACL name to the WLC) which have been pre-configured on the WLC to the endpoint.
PAN, MnT, and PSN must have in a Cisco ISE deployment. pxGrid is an optional persona that you may choose not to include or to include in your deployment if sharing of context-sensitive information between Cisco ISE and other network systems (i.e. Firepower, Stealtwatch, WSA, F5, Fortinet, LogRhythm, McAfee, Checkpoint RSA, Qualys etc) is required
Modes of connection of Endpoints to Cisco ISE
- Secured Wired Access
- Secured Wireless Access
- Remote Access VPN








No comments:
Post a Comment