"My
organization wants to authenticate the machine AND the user."
Quote is something that I am hearing all
the time from customers and implementers all over the world!
802.1x can be configured to support both user and machine authentication in a Windows environment.
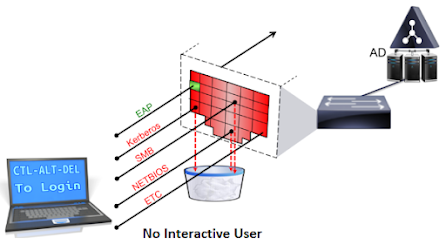
- Figure 1 is meant to illustrate a Windows Computer connecting to an 802.1X enabled network. Since 802.1x was designed to authenticate the USER, the machine is still sitting there waiting for an interactive user to press CTL-ALT-DEL and log in.
- Since there is no interactive user, there would be no "Identity" to send into the network for authentication & now this machine is sitting there without any ability to reach Active Directory for Group Policy (GPO) updates, or other important endpoint management tasks.
This is Where
Microsoft Does Something Very Cool
When a Windows desktop machine joins Active Directory, there is a
computer account that gets created and a unique password is negotiated between
the machine and AD.
Figure 2 shows a screen shot from Active Directory Users and Computers
showing the domain joined computer accounts.
- This computer account can now be used to identify the machine, even when no user is logged in, which can be used to provide the machine access to the network. This is what we commonly call a "machine auth".
- Machine authentication is used to ensure that a computer connecting to the network is a trusted device.
- Machine authentication will be performed when the login screen appears, either during boot-time or when you log out, that is when no user is logged in.
- You can get to the login or sign-in screen by signing out or rebooting your computer.
- Putting a computer to sleep, hibernating a computer, or locking a screen does not trigger machine authentication.
- This machine/computer account is what the computer will use for machine authentication.
- In summary, machine authentication is simply to check if the computer connecting to the corporate network is a domain computer or not.
What About
When a User Logs In?
The computer is on the network, and able to communicate.
What happens when a user sits down &
presses CTL-ALT-DEL and logs into the laptop?
- Most of the time, the Windows device will send a new "start" message into the network to initiate a new network login, this time using the User-Credentials.
- Windows is a multi-user operating system.
- This is important to note, because each user will have their own credential store on the same computer. This means that employee1 will have his/her certificates and other credentials in a totally different location than employee2 & each user will not have access to anyone's credentials except their own.
- This concept is very different from the Android and iOS devices of today, which are mostly single-user devices.
- When the user logs into the Windows machine, the "state" changes & uses their credentials.
- There is an option to keep the machine state for the network authentication, but there is no option in native Windows for the user state to extend beyond logoff, or to validate both the machine and the user credentials.
- Computer authentications are possible because Microsoft creates a computer-account in Active Directory which both the PC and AD are aware of, thereby allowing the computer to have its own identity for network access purposes (among other things).
- When a user logs in, the context of the system on the network changes, and a new EAP authentication occurs, thereby changing the authentication on the port to a user-based authentication

No comments:
Post a Comment