In this section, we're going to look at VLANs or virtual
local area networks.
We're going to virtualize our infrastructure.
Virtualization is a big topic today with companies such as
VMware virtualizing servers.
But VLANs have been around for many years. And in a similar
way, we're going to be virtualizing our switches where one physical switch is
virtually multiple switches. This is not full virtualization. We're just
virtualizing the local area networks on that specific switch.
What is Virtual LAN (VLAN)?
- In a switched network, you might have different user groups like management, tech support, payroll and device groups like printers, workstations, or access points. By default, all interfaces on a switch can communicate with each other so it’s difficult to make a separation unless you use a different physical switch for each group of users/devices.
- VLANs allows us to create virtual groups on our switch. We assign interfaces to different groups and only the interfaces in the same group can communicate with each other.
A VLAN is essentially a single broadcast domain or logical subnet
or logical network.
You could say it's a group of hosts with a common set of
requirements attached to the same broadcast domain.
- By default, a switch will forward both broadcasts and multicasts out every port but the originating port. However, a switch can be logically segmented into separate broadcast domains, using Virtual LANs (or VLANs).
- Each VLAN represents a unique broadcast domain:
- Traffic between devices within the same VLAN is switched.
- Traffic between devices in different VLANs requires a Layer-3 device to communicate.
Thus, a switch that supports VLANs is not necessarily a Layer-3 switch. However, a purely Layer-2 switch cannot route between VLANs.
Remember, though VLANs provide separation for Layer-3 broadcast
domains, they are still a Layer-2 function. A VLAN often has a direct
relationship with an IP subnet, though this is not a requirement.
Advantages of VLAN
- Segmentation: For instance, the sales department will go into specific VLAN, and the accountancy department will go into different VLAN.
- VLANs can improve performance for devices on them by reducing the amount of traffic a given endpoint sees and processes. VLANs break up broadcast domains, reducing the number of other hosts from which any given device sees broadcasts. For example, if all desktop voice over IP phones is on one VLAN and all workstations are on another, phones won't see any workstation-generated broadcast traffic and vice versa. Each can devote its network resources to relevant traffic only.
- Flexibility: Without changing physical cabling, you can move a user from one VLAN to another.
- Security: It also provides security because users are in separate VLANs and therefore have to traverse a layer 3 device like a router to get from one VLAN to another. On the router you can implement access lists to control which users have access to various VLANs.
- Ease Administration: Using VLANs to group endpoints also enables administrators to group devices for purely administrative, nontechnical purposes. For example, they may put all accounting computers on one VLAN, all human resources computers on another and so on.
Paradigm
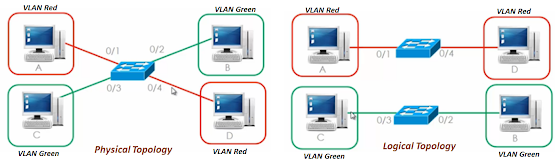
- Something that I find that always confuses people is the difference between a physical topology and a logical topology.
- You need to change your paradigm and no longer think about the physical topology of the network, but rather envision what the logical topology looks like.
- The logical topology will be very different to the physical topology, as soon as VLANs are implemented. So, he has an example of what a physical topology may look like.
- You have four physical machines connected to a single physical switch on ports 0/1, 0/2, 0/3, 0/4.
- So that's the physical topology.
- However, logically we can put interfaces into different VLANs.
- By default, all ports belong to VLAN one on Cisco switches, but by using a single command you can move that port to a separate VLAN.
- So, all you need to do is go onto the interface put that interface into a specific VLAN.
- Let say, interface 0/1 and 0/4 of switch are put in VLAN Red, and 0/2 and 0/3 are put in VLAN Green.
- These mean PC-A and PC-D are in VLAN Red, and PC-B and PC-C are in VLAN Green.
- So, when looking at the logical topology, things are dramatically different.
- Logically, there are two separate switches or two separate LANs.
- Here we have virtualized our LAN infrastructure and created two separate local area networks.
- These networks cannot communicate with each other from a layer two point of view.
- VLANs are implemented at layer two and the only way to move from one VLAN to another is to go via a layer three device such as a router.
VLAN Port Types
- A VLAN-enabled switch supports two types of ports:
- Access ports
- Trunk ports
Any host connected to an access port immediately becomes a member of the VLAN configured on that port. This is transparent to the host - it is unaware that it belongs to a VLAN.
It is possible for a VLAN to span more than one switch. There are two methods of connecting a VLAN across multiple switches:
- Create uplink access ports between the switches, one for each VLAN.
- Create a trunk connection between the switches.
Trunking Protocol
- A special type of link is required between the two switches so that they can communicate VLAN information between them and that is known as a trunk port.
- This interface will run a trunking protocol so that VLAN information can be transmitted from one switch to another.
- Trunking allows multiple VLANs to traverse a single physical link.
- When VLANs span multiple switches, a mechanism is required to identify which VLAN a frame belongs to. This is accomplished through frame tagging, which places a VLAN ID in each frame.
- Tagging only occurs when a frame is sent out a trunk port. Traffic sent out access ports is never tagged.
- VLAN trunks can be used to extend multiple broadcast domains (i.e., VLANs) between two switches by utilizing only a single physical link.
- Ethernet frames must be embedded with some kind of VLAN identifier when travelling across a VLAN trunk
- Cisco switches support two frame tagging/trunking protocols:
- ISL (Inter-Switch Link)
- 802.1Q
- Cisco IP phones, for example, do not support ISL and a lot of new switches do not provide support for ISL.
Inter-Switch Link (ISL)
- Inter-Switch Link (ISL) is Cisco’s proprietary frame tagging protocol.
- ISL supports several technologies:
- Ethernet
- Token Ring
- FDDI
- ATM
- ISL encapsulates a frame with an additional header (26 bytes) and trailer (4 bytes). Thus, ISL increases the size of a frame by 30 bytes.
- The header contains several fields, including a 15-bit VLAN ID. The trailer contains an additional 4-byte CRC to verify data integrity.
- Normally, the maximum possible size of an Ethernet frame is 1518 bytes. This is known as the Maximum Transmission Unit (MTU). Most Ethernet devices use a default MTU of 1514 bytes.
- ISL increases the frame size by another 30 bytes. Thus, most switches will disregard ISL-tagged frames as being oversized and drop the frame. An oversized frame is usually referred to as a giant. Somewhat endearingly, a slightly oversized frame is known as a baby giant.
- Cisco switches are specifically engineered to support these giant ISL – tagged frames. Note that this is a key reason why ISL is Cisco-proprietary.
- ISL supports a maximum of 1000 VLANs on a trunk port. ISL is also almost entirely deprecated - most modern Cisco switches no longer support it.
IEEE 802.1Q
- IEEE 802.1Q, otherwise referred to as dot1Q, is an industry-standard frame-tagging protocol.
- 802.1Q is supported by nearly all switch manufacturers, including Cisco.
- Because 802.1Q is an open standard, switches from different vendors can be trunked together.
- Recall that ISL encapsulates a frame with an additional header and trailer. In contrast, 802.1Q embeds a 4-byte VLAN tag directly into the Layer-2 frame header. Because the Layer-2 header is modified, 802.1Q must recalculate the frame’s CRC value.
- The VLAN tag includes a 12-bit VLAN ID. This tag increases the size of an Ethernet frame, from its default of 1514 bytes to 1518 bytes. Nearly all modern switches support the 802.1Q tag and the slight increase in frame size.
- 802.1Q supports a maximum of 4096 VLANs on a trunk port.
- As shown in Figure, in the header of a traditional Ethernet packet, the field after the destination MAC address and the source MAC address (DA & SA) field is the Type field, which indicates the upper layer protocol type.
- IEEE 802.1Q inserts a four-byte VLAN tag between the DA&SA field and the Type field to identify the VLAN information, as shown in Figure.
The fields of a VLAN tag are TPID, priority, CFI, and VLAN ID.
- TPID - The 16-bit TPID field indicates whether a frame is VLAN-tagged. By default, the TPID value is 0x8100, which indicates that the frame is VLAN-tagged. Device’s vendors can set the TPID to different values. For compatibility with these devices, modify the TPID value so that frames carry a TPID value identical to the value of a particular vendor, allowing interoperability with devices from that vendor. The device determines whether a received frame carries a VLAN tag by checking the TPID value. When the TPID value of a frame is the configured value or 0x8100, the frame is considered as a VLAN-tagged frame.
- Priority - The 3-bit priority field indicates the 802.1p priority of the frame. This is used very heavily in quality of service where for instance, a decimal value of five is used to represent voice.
- CFI - The Canonical format identifier (CFI) was used in the old days for compatibility between Ethernet and token ring networks. It's very unlikely that you're going to use that today.
- The 1-bit CFI field indicates whether the MAC addresses are encapsulated in standard format when packets are transmitted across different media. A value of 0 indicates that MAC addresses are encapsulated in standard format. A value of 1 indicates that MAC addresses are encapsulated in a non-standard format. The value of this field is 0 by default.
- VLAN ID - The 12-bit VLAN ID field identifies the VLAN that the frame belongs to. The VLAN ID range is 0 to 4095. Because 0 and 4095 are reserved, a VLAN ID is in the range of 1 to 4094.
When a frame carrying multiple VLAN tags passes through, the device processes the frame according to its outer VLAN tag and transmits the inner tags as payload.
The tagging protocol can be manually specified on a trunk port, or dynamically negotiated using Cisco’s proprietary Dynamic Trunking Protocol (DTP).
VLAN Range
- VLAN 0, 4095: These are reserved VLAN which cannot be seen or used. VLAN 0 is reserved for 802.1p.
- The VLAN ID 0 is used when a device needs to send priority-tagged frames but does not know in which VLAN it resides. The basic Ethernet frame does not have any priority field. The priority bits, also called CoS bits (Class of Service) are a part of 802.1Q VLAN tag. Therefore, a device needing to add a CoS marking to its frames has to insert a 802.1Q tag into each frame. However, even though this device may be capable of adding 802.1Q tags into its frames, it may not know in what VLAN it currently resides.
- This is where the VLAN ID 0 comes in. A device that sends CoS-marked frames can insert an 802.1Q tag into a frame, use the VLAN ID 0 and set the CoS marking appropriately. When a VLAN-aware switch receives this frame, the VLAN ID 0 tells it: "Put the frame in the ordinary access VLAN of the port as if it was untagged, however, process the CoS field accordingly." In other words, the VLAN ID 0 represents the access - or the native - VLAN of the receiving port, whatever VLAN that might be.
- VLAN 1: It is the default VLAN of switches. By default, all switch ports are in VLAN. This VLAN can’t be deleted or edit but can be used.
- VLAN 2-1001: This is a normal VLAN range. We can create, edit, and delete these VLAN.
- VLAN 1002-1005: These are CISCO defaults for FDDI and token rings. These VLAN can’t be deleted.
- VLAN 1006-4094: This is the extended range of VLAN.
Native VLANs
- Native VLANs are untagged when a port on the switch is set up as a trunk.
- For instance, the interface on switch 1 and switch 2, that interface can receive and transmit tagged frames. Frames belonging to the native VLAN do not carry VLAN tags when sent over this trunk.
- By the same token, if an untagged frame were received on this trunk port, that frame would automatically be associated with a native VLAN for the support.
- Now specific management traffic will go across the native VLAN.
- So, for instance spanning tree CPUs will use the native VLAN and so will dynamic trunking protocol.
- Dynamic Trunking Protocol is a way that switches negotiate to set up a trunk between themselves automatically.
- Certain management traffic always uses VLAN 1 as:
- CDP - It allows us to view directly connected devices.
- VTP - It is a way to dynamically update other switches with changes made on a single switch in a VTP domain.
- PAgP - Port aggregation protocol is a protocol used for the automatic creation of Etherchannels.
- UDLD - Directional link detection is used to monitor the physical configuration of cables between devices and detect unidirectional links. This allows us to detect incorrectly cabled links.
The important thing to take note of here is that on trunk links there is a special VLAN known as the native VLAN where traffic is sent untagged if left at the default of VLAN one.
- A lot of management traffic will be sent across that native VLAN. It's important that the native VLAN on both sides of the trunk be the same.
- If they not set the same. The switches will notify you by telling you that there's a native VLAN mismatch.
- The issue that arises if the native VLANs are not the same is that traffic from one VLAN on this switch will automatically be associated and end up in a different VLAN on another switch. \
- And obviously the whole concept of VLANs is to separate traffic into a specific VLAN.
By default, on all trunking ports, the native VLAN is VLAN
1. The native VLAN can be changed on a per trunk port basis:
Switch(config)# interface gi2/24Switch(config-if)# switchport mode trunkSwitch(config-if)# switchport trunk native vlan 42
Native VLANs pose a security risk, allowing an attacker to
hop to another VLAN by double-tagging a frame. This can be mitigated by
changing the native VLAN to an unused or disabled VLAN. A better solution is to
force trunk ports to tag native VLAN traffic - globally or on a per-trunk
basis:
Switch(config)# vlan dot1q tag nativeSwitch(config)# interface gi2/24Switch(config-if)# switchport trunk native vlan tag
The Default VLAN is simply the VLAN which all Access Ports
are assigned to until they are explicitly placed in another VLAN.
So, to summarize:
The Native VLAN can
change. You can set it to anything you like.
The Access Port VLAN
can change. You can set it to anything you like.
The Default Native
VLAN is always 1, this cannot be change, because its set that way by Cisco.
Common implementation of native VLANs in the real world today.
What is more typical today is a scenario like this where you
have a PC connected to an IP phone connected to a Cisco switch.
- Now a Cisco IP phone has a built-in three-way switch.
One port is connected back to the network infrastructure, i.e., our Cisco switch, a second port allows the PC to connect to the infrastructure through the phone and a third port allows for voice traffic from the handset to be prioritized over data when sent to the network infrastructure.
- So, the phone has a built-in three-way switch, always prioritizing voice over data.
- The thing to take note of here, though, is that the phone can be configured in a separate VLAN to the PC, so the phone could be in the red VLAN, and the PC could be in the green VLAN.
- There are a lot of advantages to doing it this way.
- From a security point of view, this PC will not be able to sniff voice traffic and therefore listen in on the voice conversation.
- From a quality-of-service point of view, it's easier to prioritize the voice traffic over the data traffic.
- It has easier IP address management because you can assign a separate subnet to your phones versus your PCs and thus scale your IP address.
- So, what happens is the switch is configured with what's called a voice VLAN and a native VLAN.
- The voice VLAN is tagged, so tagged frames get sent to the phone and the phone with its built-in three-way switch is able to read the attitude of one dot1Q frames, untagged frames are sent on what's called the native VLAN or data VLAN.
- That information is sent to the phone and the phone just switches that to the PC.
- So, the PC receives the untagged or native VLAN frames and the phone receives the tagged or voice VLAN frames.
- No configuration of the phone is necessary to enable this.
- You literally type a few commands on the switch, telling the switch what the voice VLAN is and what the data VLAN is.
- And this happens automatically because when the phones boot up they query the switch through CDP to find out which VLAN they belong to.
- So, the switch updates the phone's configuration through the use of CDP.
How Port is assigned to VLANs?
VLAN membership can be configured one of two ways:
- Static VLAN - Firstly, they can be statically assigned by an administrator. So, as an administrator, go on to an interface and statically put that port into a VLAN.
- Dynamic VLAN - Dynamic VLANs allow for a ports VLAN to be dynamically updated based on the Mac address of the device attached to that port.
- So, in a boardroom, for example, when a director plugs in a laptop based on the Mac address of that laptop, that port is dynamically assigned to the director's VLAN.
- When a manager plugs his laptop into that same port the next day, for example, that VLAN is automatically updated to the manager's VLAN.
- So, based on the source MAC address of frames received on the port, the port is automatically assigned to different VLANs.
- Voice VLAN - And lastly, we have voice VLANs, which are used specifically for IP phones.
Basic VLAN Configuration
Working with VLANs is a two-step
process:
Create VLAN number globally
Switch(config)#vlan <vlan-number>Apply VLAN to switchport
Switch(config-vlan)#name <descriptive name>
Switch(config)#interface <type/value>
Switch(config-if)#switchport access vlan <vlan-number>
VLAN Trunk Configuration
- Interfaces can be configured to trunk using two methods:
- Static/manual trunking
- Dynamic negotiation of trunking with peer switch
Switch(config-if)#switchport trunk encapsulation (isl | dot1q)Force interface into trunking mode:
Switch(config-if)#switchport mode trunkChange Native VLAN value:
Switch(config-if)#switchport trunk native vlan <vlan-id>Restricting allowed VLANs on trunk:
Switch(config-if)#switchport trunk allowed vlan <add | all | except | none | remove> <vlan-list>Tagging the 802.1q Native VLAN:
Switch(config)#vlan dot1q tag native
- Confirm that neither side of trunk is Admin Down
- If one (or both) sides display as “Up/Down” or “Down/Down”:
- Check that speed/duplex match on both sides
- Check cabling
- Confirm both sides of trunk are using the same encapsulation type.
- Confirm that Native VLAN matches on both sides
- Confirm that both sides of the trunk are allowing the same VLANs
- Confirm matching VTP Domain Name
- Recall that a trunk’s frame tagging protocol can be auto negotiated, through the use of the Dynamic Trunking Protocol (DTP).
- DTP can also negotiate whether a port becomes a trunk at all. Previous examples demonstrated how to manually configure a port to trunk:
Switch(config)# interface gi2/24DTP has two modes to dynamically decide whether a port becomes a trunk:
Switch(config-if)# switchport mode trunk
- Desirable – the port will actively attempt to form a trunk with the remote switch. This is the default setting.
- Auto – the port will passively wait for the remote switch to initiate the trunk.
Switch(config)# interface gi2/24Trunk ports send out DTP frames every 30 seconds to indicate their configured mode.
Switch(config-if)# switchport mode dynamic desirable
Switch(config-if)# switchport mode dynamic auto
DTP can be utilized in three
modes:
- ON: Trunk is statically created but still transmits DTP
- Desirable: Port remains in “Access Mode” while initiating DTP requests for trunking
- Auto: Port remains in “Access Mode” while passively listening for DTP
- manual trunk <-----> manual trunk
- manual trunk <-----> dynamic desirable
- manual trunk <-----> dynamic auto
- dynamic desirable <-----> dynamic desirable
- dynamic desirable <-----> dynamic auto
It is best practice to manually configure trunk ports, to avoid DTP negotiation errors. DTP is also vulnerable to VLAN spoofing attacks.
To explicitly disable DTP:
Switch(config)# interface gi2/24
Switch(config-if)# switchport mode trunk
Switch(config-if)# switchport nonegotiate
DTP Sniffer Trace
Dynamic Trunk Troubleshooting
- Same initial troubleshooting steps as those performed with static VLAN trunks
- Check that DTP modes on both sides of trunk are suitable for trunking
- Remember that DTP cannot be used when trunking to:
- Non-Cisco devices
- Cisco Routers
- DTP carries the VTP domain name, so ensure this parameter matches on both sides of potential trunk






No comments:
Post a Comment