As we have learned that VLANs are locally significant for a switch and are configured manually. Well, if you think more deeply about it, this is a huge scaling limitation. Imagine a network that has 100+ switches and you want to provision a new VLAN. Someone must log on every single device and execute the commands. This is a slow and trivial process prone to human error. The VLAN Trunking Protocol (VTP) has been introduced to solve this scaling problem.
VLAN Trunking Protocol is a Cisco proprietary layer two
protocol which allows for the propagation of VLAN information from one switch
to another rather than TELNET to multiple switches.
You can create, delete, or rename VLANs on one switch and have
that information automatically propagated to other switches across trunk links. Notice the name VLAN Trunking protocol. This information can
only be propagated across trunk links. VTP advertisements can be
sent over 802.1Q, and ISL trunks.
To better understand the true value of VTP, consider an example network with 100 switches.
- Without VTP, if you want to create a VLAN on each switch, you will have to manually enter VLAN configuration commands on every switch! VTP enables you to create the VLAN only on a single switch.
- That switch can then propagate information about the VLAN to every other switch on the network and cause other switches to create it.
- Likewise, if you want to delete a VLAN, you only need to delete it on one switch, and the change is automatically propagated to every other switch inside the same VTP domain.
The following network topology explains the concept more
thoroughly:
- On SW1, we have created a new VLAN. SW1 sends a VTP update about the new VLAN to SW2, which in turn sends its VTP update to SW3.
- These updates will cause SW2 and SW3 to create the same VLAN.
- You can see how this simplifies network administration – the engineer only had to log in and create the VLAN on the first switch.
- Other switches have created the same VLAN automatically.
NOTE
VTP does not advertise information about which switch ports are
assigned to which VLAN.
VTP Versions
There are three versions of VTP.
VTP Version 1
VTP version 1 supports the
following features:
- The default for old Cisco switches.
- VTP transparent switch relay VTP messages only if the domain and version found in the message are equal to its own.
- It supports only the normal VLAN range (1-1005) even in Transparent mode.
- It drops unknown TLVs (Type-Length-Value).
VTP version 2 has the following improvements over version 1:
- The default for modern Cisco switches.
- VTP transparent switch relay VTP messages without inspecting the domain name and version number.
- It supports extended VLANs range (1006 to 4094) in Transparent mode.
- When new information is received from VTP messages, consistency checks are not performed. If the MD5 digest on a received VTP message is correct, the information is accepted.
- It relays unknown TLVs (Type-Length-Value).
VTP version 3 has many important features and improvements over v1 and v2 such as:
- VTP primary server: only the primary server can create / modify / delete VLANs. This is a great change as you can no longer “accidently” wipe all VLANs like you could with VTP version 1 or 2.
- This is a feature/role introduced in VTP Version 3
- Before V3, if a Switch with a higher Revision Number was added to the network, it had the capability to wipe the entire network’s VLAN configuration from all Switches
- This is clearly undesirable behavior and is why the Primary Server feature was developed
- When a Switch is configured as the Primary Server, only it can make new VLANs
- Even if another Switch is configured as a VTP server, it won’t be able to make new VLANs, this is reserved for the Primary Server only
- This eliminates the previously mentioned problem and provides some VTP stability and reliability
- Extended VLANs: you can now synchronize VLANs in the extended VLAN range (1006 – 4094).
- Private VLANs: if you have VLANs that are configured as private VLANs then you can synchronize them with VTPv3.
- RSPAN VLANs: remote SPAN VLANs can now be synchronized.
- MST Support: one of the problems of MST is that you had to configure each switch manually. With VTPv3, MST configurations are synchronized.
- Authentication improvements: VTPv3 has more secure methods for authentication.
- VTP mode off: If you didn’t want to use VTP for version 1 or 2 then you had to use the transparent mode. VTPv3 can be disabled globally or per interface.
- Compatibility: VTP version 3 is compatible with version 2, not version 1.
- Ability to enable VTP on a per-port basis.
VTP Modes
A switch using VTP must operate in
one of four modes:
VTP Server mode:
- A switch using this mode can create and delete VLANs. A VTP server switch will propagate VLAN changes.
- This is the default mode for Cisco switches.
Switch(config)#vtp mode serverVTP Client mode:
Switch(config)#vtp domain rjsnetworkcloudacademy
Switch(config)#vtp password rjs
- A switch using this mode can’t change its VLAN configuration.
- That means that a VTP client switch cannot create or delete VLANs.
- However, received VTP updates are processed and forwarded.
Switch(config)#vtp mode client
VTP Transparent mode:
- A switch using this mode doesn’t share its VLAN database, but it forwards received VTP advertisements.
- You can create and delete VLANs on a VTP transparent switch, but these changes will not be sent to other switches.
Switch(config)#vtp mode transparentTransparent switches will pass through advertisements from other switches in the VTP domain.
The VTP version dictates how the pass through is handled:
- VTP version 1 – the transparent switch will only pass-through advertisements from the same VTP domain.
- VTP version 2 – the transparent switch will pass through advertisements from any VTP domain.
- Like VTP transparent mode, with a difference that a switch using this mode will not forward received VTP updates.
- This command is supported only in VTP V3.
Consider the following example:
We have a simple network of three
switches.
- SW1 is configured as VTP server.
- After the VLAN 5 is created on SW1, this switch will notify the connected switch (SW2) about the created VLAN.
- SW2 will receive the update but, since it uses the VTP transparent mode, it will not create this VLAN in its configuration.
- However, it will forward the VTP update to SW3.
- Since SW3 is configured as VTP client, it will process the update and create VLAN 5.
VTP Operation
VTP Domain Name:
- A VTP domain is defined by all switches that share the same VTP Domain name. A switch can be in only one domain.
- By default, Cisco switches do not have a VTP domain name assigned. When they receive a VTP advertisement over a trunk link, they inherit the domain name and the VTP revision number found in the message. The name can be configured manually using the vtp name command.
- All changes made on the VTP server are propagated only to the switches in the VTP domain. If there is a switch configured with different VTP domain name, it won't accept the advertisements and won't update its VLAN database.
Plaintext authentication password:
Switch(config)#vtp password <password>

Plaintext entry but stored as
hashed digest:
Switch(config)#vtp password <password> hidden
Entry of pre-hashed authentication
password:
Switch(config)#vtp password <hashed-digest> secret
VTP Configuration Revision:
Switches use the VTP Revision Number to keep track of
domain's VLAN database changes. It starts from 0 and for every change (VLAN
added, VLAN deleted etc), the number is increased by 1 and is advertised to all
other VTP clients in the domain. Therefore, all switches in a VTP domain must
have the same revision number at any given time. If a switch receives a VTP
message, it only processes the data if the revision number in the update is
higher than its own.
VTP advertisements are marked with a 32-bit
configuration revision number, to identify the most current VLAN
database revision. Any change to the VLAN database increments the configuration
revision number by 1. Thus, a higher number represents a newer database
revision.
Important note: While only VTP servers can change the
VLAN database, VTP clients can advertise updates, to other clients and even to
a server! If the revision number is higher, the switch will accept the update.
- This can result in a newly introduced switch advertising a blank or incorrect VLAN database to all other switches in the domain. Switch ports would then lose their VLAN memberships, resulting in a significant network outage.
- This can be avoided when implementing a new switch into the VTP domain.
- Best practice is to configure a new switch as a VTP client and reset its revision number to zero before deploying into a production network.
- There are two methods of resetting the revision number to zero on a switch:
- Change the VTP domain name, and then change it back to the original name.
- Change the VTP mode to transparent, and then change it back to either server or client. Transparent switches always a revision number of 0.
VTP Message Types
VTP messages carried between switches on VLAN trunks.
Three message types exist for VTP advertisements:
- Summary Advertisement
- Subset Advertisement
- Advertisement Request
Used as a VTP Keepalive.
Summary advertisements contain the following information about the VTP domain:
- VTP version
- Domain name
- Configuration revision number
- Time stamp
- MD5 digest
The summary is then followed with a subset advertisement, which contains the full, updated VLAN database.
Contains list of all known VLANs and associated VLAN details
A subset advertisement will contain the following information:
- VTP version
- Domain name
- Configuration revision number
- VLAN IDs for each VLAN in the database
- VLAN-specific information, such as the VLAN name and MTU
Important note: Switches
will only accept summary and subset advertisements if the domain name and MD5
digest match. Otherwise, the advertisements are ignored.
If a switch receives a summary advertisement with a
revision number higher than its own, it will send out an advertisement
request.
VTP servers will then respond with an updated summary and
subset advertisement so that the switch can synchronize to the most current
VLAN database.
A switch that is reset or newly joined to the VTP domain
will also send out an advertisement request.
Summary-Advert Frame Format
Version | Code | Followers | Management | Management | Configuration | Updater | Update | MD5 |
Subset-Advert Frame Format
Version | Code | Sequence Number | Management | Management | Configuration | VLAN | VLAN | … | VLAN |
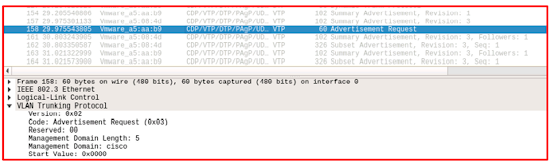
Advert-Request
Frame Format
|
Version |
Code |
Reserved |
Management |
Start value |
The Code field indicates the message type. Possible values are:
- 0x01—Summary-Advert
- 0x02—Subset-Advert
- 0x03—Advert-Request
VTP Pruning
- Recall that Layer-2 switches belong to only one broadcast domain.
- A Layer-2 switch will thus forward both broadcasts and multicasts out every port in the same VLAN but the originating port.
- This includes sending out broadcasts out trunk ports to other switches, which will in turn flood that broadcast out all ports in the same VLAN.
- VTP pruning eliminates unnecessary broadcast or multicast traffic throughout the switching infrastructure.
- Consider the following example:
- Assume that a host is connected to SwitchB, in VLAN 300.
- If the host sends out a broadcast, SwitchB will forward the broadcast out every port in VLAN 300, including the trunk ports to SwitchA and SwitchC.
- Both SwitchA and SwitchC will then forward that broadcast out every port in VLAN 300.
- However, SwitchA does not have any ports in VLAN 300, and will drop the broadcast.
- Thus, sending the broadcast to SwitchA is a waste of bandwidth.
- VTP pruning allows a switch to learn which VLANs are active on its neighbors.
- Thus, broadcasts are only sent out the necessary trunk ports where those VLANs exist.
- In the preceding example, pruning would prevent VLAN 300 broadcasts from being sent to SwitchA, and would prevent VLAN 100 and 200 broadcasts from being sent to SwitchC.
- VTP pruning is disabled by default on IOS switches.
- VTP pruning must be enabled on a server, and will be applied globally to the entire VTP domain:
Switch(config)# vtp pruning
- Both VLAN 1 and the system VLANs 1002-1005 are never eligible for pruning. To manually specify which VLANs are pruning eligible on a trunk:
Switch(config)# interface gi2/24
Switch(config-if)# switchport trunk pruning vlan 2-10
Switch(config-if)# switchport trunk pruning vlan add 42
Switch(config-if)# switchport trunk pruning vlan remove 5
Switch(config-if)# switchport trunk pruning vlan except 100-200
Switch(config-if)# switchport trunk pruning vlan none
VTP Configuration
VTP v1 & v2 Configuration
- Configure VTP domain name (case sensitive)
Switch(config)#vtp domain [name]
- Configure VTP version
Switch(config)#vtp version 2
- Configure VTP mode
Switch(config)#vtp mode [client | server | transparent]
- Configure VTP authentication (optional)
Switch(config)#vtp password <password>
VTP v3 Configuration
- Configure VTP domain name (case sensitive)
Switch(config)#vtp domain [name]
- Configure VTP version
Switch(config)#vtp version 3
NOTE: This defaults the switch to a VTP Secondary Server
- Configure VTP mode
Switch(config)#vtp mode [client | server | transparent]
- Configure VTP Primary Server
Switch#vtp primary [force | mst | vlan]
VTP Verification
- Show vtp status
- Show vtp counters
- Show vtp password
- Show vtp interface
VTP Issue
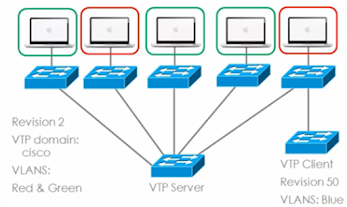
Notice we have a VTP server and let's assume that all of
these switches at the top are configured as VTP clients.
- The host machines are in the red VLAN or green VLAN, and currently the revision number for the domain is revision number two.
- So, the latest configuration revision number is to the VTP domain is Cisco and the VLANs that have been configured on the switches of VLANs, red and green.
- Please note once again that the switches have a VLAN database.
- That is what VTP updates, the individual ports on the switches need to manually be put in the correct VLANs.
- Now someone plugs another switch into the topology from, for instance, a lab environment.
- The reason why this is dangerous is that in a lab environment, VLANs may have been added and removed and thus the revision number may be a lot higher than the production network.
- So, let's assume for the moment that the revision number is 50.
- This switch only has the blue VLAN configured on it, so the green and red vlans do not exist in the VLAN database.
- A lot of people make the mistake of assuming that as long as the switch is configured as a VTP client, it will not cause any problems on the network. So, an administrator plugs in the switch and configures this port as a trunk.
- Please note once again that VDP advertisements are only sent across trunk ports. So, let's assume that throughout the network all of these links are configured as trunks.
- As soon as this client is added to the VTP domain.
- And what's really scary is that this client can be automatically updated with the VTP information.
- In other words, if it's configured with a null domain, it can automatically join the current VTP domain of Cisco.
- And as soon as that happens, the devices will synchronize their databases to the latest configuration revision number, which in this case is 50.
- So, on all switches in the live domain, the revision number is changed to 50 because all of the switches, including the VTP server, will synchronize automatically to the VTP client.
- The current VLANs, red and green are automatically removed from the VLAN database and the only VLAN that will now be available in the VLAN databases of all of these switches is VLAN blue.
- Now all of the ports on, all the switches that have manually been put into the green or red VLAN are error disabled. The issue here is that a port belongs to the red VLAN, but the red VLAN does not exist in the database, so, the port is automatically disabled.
- That means that no traffic can be sent or received on this port and the same thing happens on all other switches.
- Essentially what happens is that the entire network is brought down by the introduction of the single switch. That's extremely worrying, to say the least, that the introduction of a single switch can bring down an entire enterprise network.
- The only way to fix this is to physically connect to the HTTP server and then manually add the VLANs that have been deleted.





No comments:
Post a Comment